How proxies work
In a nutshell, what you’re doing with a proxy is setting up a middle-person between you and the internet. Using the proxy, your browser hands off web page requests to the proxy server, which handles the request and fetches the page for you from the internet. The web site actually thinks the request is coming from the proxy server, not your computer, which is a good way to obscure your originating IP address.
Additionally, the connection between your computer and the proxy happens over SSH, an encrypted protocol. This prevents wifi sniffers from seeing what you’re doing online.
What you’ll need
An SSH server to act as your proxy.
Simple enough really! If you’re using windows I highly recommend freeSSHD (available here). If you’re on a mac check out this page for instructions on how to enable remote logon. Linux users, you should know how to do this.
An SSH client on the computer you’re using.
Mac and linux machines have SSH built right in at the command line. Windows users you can download plink (available here).
Simple enough really! If you’re using windows I highly recommend freeSSHD (available here). If you’re on a mac check out this page for instructions on how to enable remote logon. Linux users, you should know how to do this.
An SSH client on the computer you’re using.
Mac and linux machines have SSH built right in at the command line. Windows users you can download plink (available here).
How to set up freeSSHd
- Double click the freeSSHd installer that you have downloaded to get started.
- Click Next -> Click Next (or you can change the default installation directory) -> Click Next (Full Installation) -> Click Next (Start Menu Folder) -> Click Next (Create a desktop icon) -> Click Install (ready to install) -> Wait until installation has been finished -> Click Close
- Do you want to run freeSSHd as a system service?” I choose “No” so I can start freeSSHd manually. This is a good security practice because you don’t want to have running applications in the background if you are not using it. Only turn freeSSHd on when the need for remote connections arise!
- Click Finish to complete freeSSHd installation. (Duh simple enough even a caveman can do it)
- Double click the freeSSHd icon on the desktop to load your SSH server. You can see the freeSSHd icon on your system tray.
- Right click on the icon located on the taskbar lower right hand corner and click Settings.
- Make sure that the freeSSHd settings page (Server Settings tab) shows that your“SSH server is running”.
- Click on the Users tab. You need to create at least one user account that will act as your SSH remote user account.
- Click “Add” to create a new user. Fill in the user details, following the example shown below (with your own unique username and password, duh!). Click OK and make sure it appear on the Users tab list
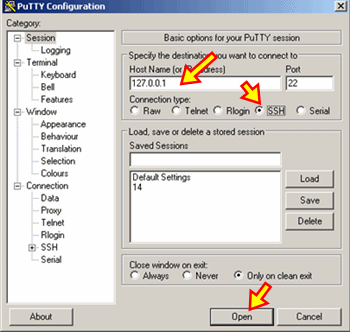
- Using the same computer that you install freeSSHd previously, download Putty (available here). Putty is a desktop command line client that you can use to access SSH servers.
- Double click the Putty installer to run it. Fill in the details as shown in the diagram below. 127.0.0.1 means that you are testing the SSH access from a local connection.
Press “Yes” on the security alert screen. Insert your SSH username and password that you have created previously.
If you get a Windows command prompt, you have successfully access your SSH server! Congratulations! Woot, Woot!
If you get a Windows command prompt, you have successfully access your SSH server! Congratulations! Woot, Woot!
Start your SSH tunnel
So you’ve got your ssh server setup at your house or workplace. Great! To connect to it we’re going to setup a local proxy server on your client that you’ll be browsing the internet from, which will then “tunnel” web traffic from your local machine to the remote server over SSH.
Connecting using your Mac/Linux
The command to run on your linux / mac client in a terminal window is:
sssh -ND 9999 you@example.comsh
sssh -ND 9999 you@example.comsh
Connecting using Windows
For Windows it’s as simple as browsing to the directory you saved plink to and runningplink.exe
-N -D 9999 you@example.com
Of course, you’re going to replace the you with your username on your SSH server and example.com with your server domain name or IP address.
What that command does is accept requests from your local machine on port 9999 and hands that request off to your server at example.com for processing.
-N -D 9999 you@example.com
Of course, you’re going to replace the you with your username on your SSH server and example.com with your server domain name or IP address.
What that command does is accept requests from your local machine on port 9999 and hands that request off to your server at example.com for processing.
When you execute either of those commands, you’ll be prompted for your password. After you authenticate, nothing will happen. The -N tells ssh not to open an interactive prompt, so it will just hang there, waiting. That’s exactly what you want.
Set Firefox to use SOCKS proxy
Once your proxy’s up and running, configure Firefox to use it. From Firefox’s Tools menu, choose Options, and from the Advanced section choose the Network tab. Next to “Configure how Firefox connects to the Internet” hit the “Settings” button and enter the SOCKS information, which is the server name (localhost) and the port you used (in the example above, 9999.)
Save those settings and hit up a web page. When it loads, visit http://www.ipchicken.com to see if it’s using your remote ssh server to tunnel traffic. If you are, you may yell out Woot, Woot! In excitement
Save those settings and hit up a web page. When it loads, visit http://www.ipchicken.com to see if it’s using your remote ssh server to tunnel traffic. If you are, you may yell out Woot, Woot! In excitement
Also remember that you’ll need to open your firewall a bit by cracking open port 9999 on your local machine and port 22 on your server for SSH.
Let me know how things work out for you and if you have any questions on setting up in the comment section below.

No comments:
Post a Comment